Solutions
Chef Docker Compliance, Integrations & Support
Securely Scale Container Utilization in Production with Chef
Request a Demo
Docker Key Considerations for DevSecOps Teams
It’s hard to “contain” the excitement for container utilization in most organizations today. Typically containers are first adopted in development, then moved into production where they become the responsibility of operations teams to monitor and secure. This has created new challenges for the DevOps and Security teams that are typically on the receiving end of these deployments and many times have little knowledge on how the containers were built or what is in them.

Visibility, Vulnerability Management and Version Control
Visibility
Without proper image management and configuration it can be difficult to determine what is running in a live container and who has access to it.
Vulnerability Management
Without knowing what is running in a container it is more difficult to audit and remediate containers thus increasing risks.
Version Control
A lack of version control can also increase the probability of out of date images with known vulnerabilities being redeployed.
Chef’s Approach to Containers
Chef has deep experience in the distributed systems management space. We’ve created a set of solutions designed specifically to address issues large complex organizations face as they scale the use of containers in production.
Define the Application
Isolate dependencies and create a minimal build artifact from scratch that is easily inspected and audited.
Harden the System
Validate the container build process, package version, functional requirements and underlying configurations.
Secure the Pipeline
Automate security testing across all stages and block unauthorized access and artifacts.
Eliminate Container Bloat and Simplify Package Management with Strict Application Definitions
Lifting and shifting an existing application with all of its “baggage” into the container world creates bloated containers that are hard to manage and audit. Applications architected using microservices deployed via containers create a web of dependency mapping, version management and user permission challenges. Chef addresses these challenges with Chef Habitat which takes a shift-left approach to application definition and packaging that works for all applications regardless of the underlying technology.
Key features of Chef’s approach to building and supporting containers with Chef Habitat include:
- Containers that always built from scratch
- Simplified dependency updates at scale
- Support for multi-layer containers
- Ability to specify application user/group and set directory permissions
- Removal of intermediate container images after builds
- Exposure of only the correct network ports
Limit Risks with Hardened Images and Continuous Inspection of Docker Containers
Chef can inspect a Docker container via the Docker API. This provides the ability to make assertions about a live, running container without requiring any changes to the container’s contents or build process. Dashboards and reports are included in Chef Automate and enable compliance teams to see the status of systems across environments in real-time.
Common security violations that can be detected by Chef InSpec include:
- Attempts to disable security related profiles
- Attempts to write files below the /etc directory or /root
- Use of privileged containers
- Attempts to change a threads namespace
- Attempts to launch sensitive mount containers
- Attempts to change users by calling setuid
- Attempts to manipulate shell files
Drive Compliance with Curated CIS Aligned Docker Auditing Content
Chef provided content for auditing Docker containers is directly aligned to CIS (Center for Internet Security) benchmarks. This minimizes the time and effort needed to audit Docker containers. Chef Compliance for Docker features standards-based audit and remediation content, easily tuned baselines to adapt to an organization’s needs, and visibility and control across hybrid and multi-cloud environments.
Chef Compliance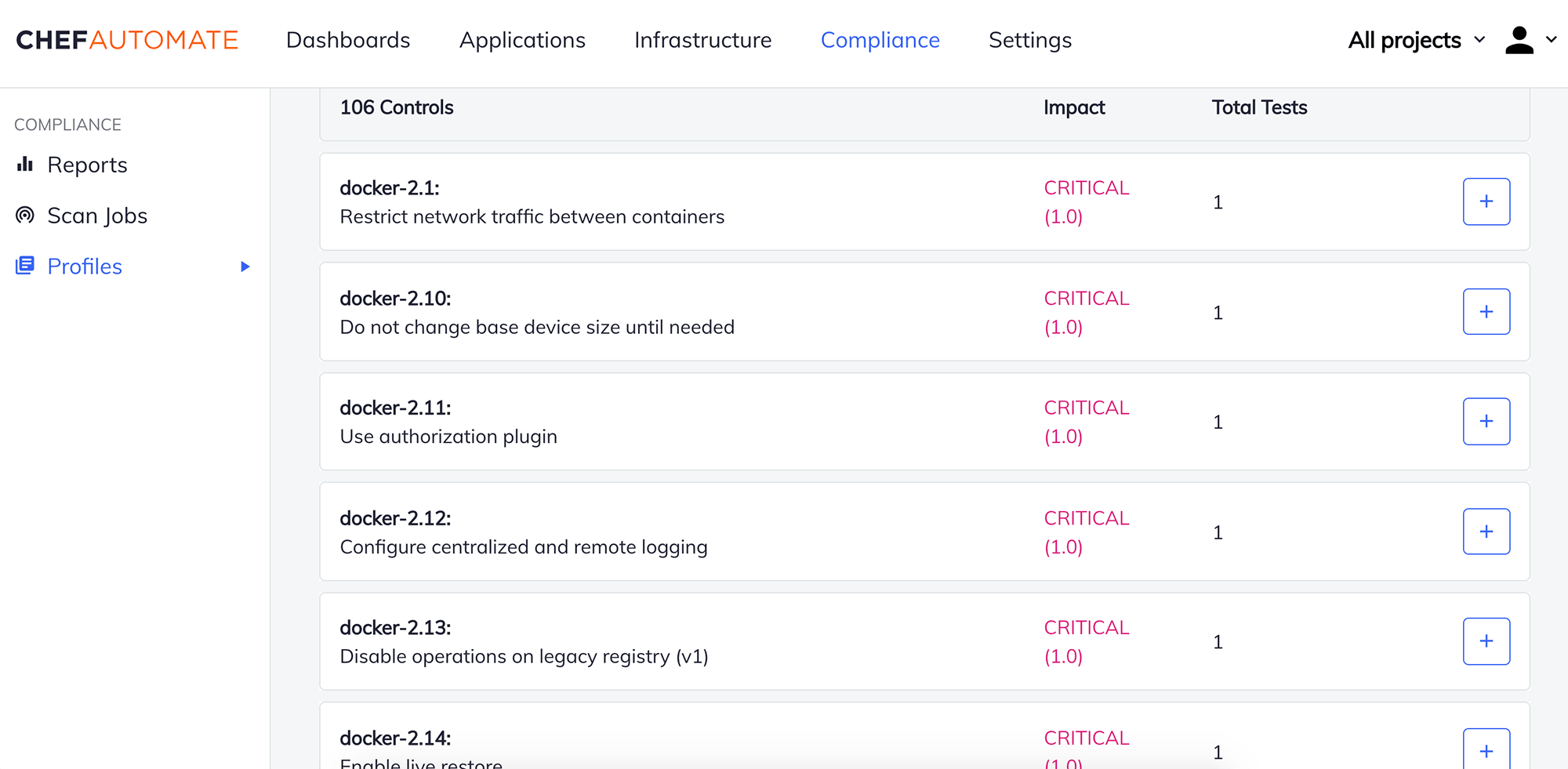
We can push a button and have a completely new VPC, with new application stacks, operational in less than 10 minutes. It has created a highly resilient ecosystem in which we’ve had zero data loss in five years.
Robust Integrations with the Leading Container Registry and Delivery Platforms

Microsoft Azure Container Registry (ACR)
Directly publish optimized packages to ACR using a native integration and streamline automated pipeline delivery.

Amazon Elastic Container Service (ECS)
Eliminate the need to build external services and add dependencies in ECS and reduce operational complexity.

Google Container Registry (GCR)
Easily build, deploy, and orchestrate Docker containers into GCR and GKE without rewriting or refactoring applications.
Ready to Scale Containers in Production?
Scaling the use of containers in production requires organizations to rethink the way they package, deliver and audit applications. By proactively addressing the questions below DevSecOps teams can help their organizations mitigate the risks of containers and accelerate adoption.
- How do you tell what processes are running in a container?
- Where do the container images come from?
- What deployments are using privileged containers?
- How frequently are the images scanned for vulnerabilities?
- How do you ensure images with known vulnerabilities are not redeployed into production?
Unsure of the answers? Our experts are here to help!
Contact Us

